Exercise 1
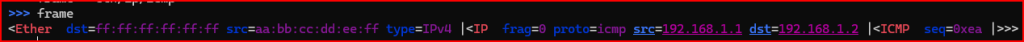
- Craft an ICMP echo request with the following:
- An Ethernet source address of
aa:bb:cc:dd:ee:ff - An Ethernet destination address of
ff:ff:ff:ff:ff:ff - A source IP address of
192.168.1.1 - A destination address of
192.168.1.2 - An ICMP sequence number of
234
- An Ethernet source address of
I am going to use a tool called scapy to complete this lab:
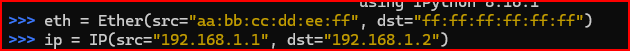
The first thing that I need to do is to create an Ethernet header and an IP header, assigning each to a variable:
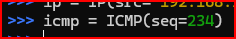
Let’s now create the ICMP sequence number:
Now that all the required headers have been built, I can assemble the frame:
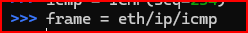
The ICMP echo request is now crafted
2. Display the frame you just created.
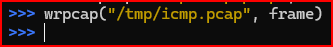
3. Write the frame you created to the output pcap file named /tmp/icmp.pcap.
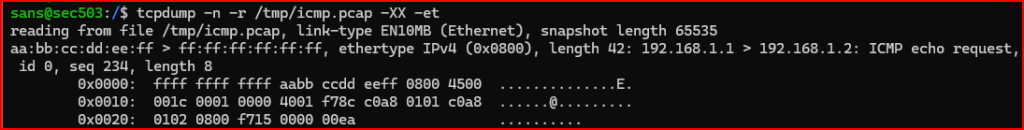
4. Use ssh to connect to the virtual machine in a second terminal window. In the new terminal, use tcpdump to examine the packet in /tmp/icmp.pcap to make sure that the frame you crafted matches the specifications detailed. With tcpdump, use either the -XX, -X, or -v option to show the link layer.
Exercise 2
- Read
/tmp/icmp.pcapthat you just created in the previous exercise using a Scapy session.
- Alter the value of the ICMP sequence number to 4321.
- Write the new record to
/tmp/icmp2.pcap. - Read
/tmp/icmp2.pcapin a different terminal (new or from the previous exercise) using tcpdump, supplying it the-vvoption to verify that you crafted a valid record.
We read /tmp/icmp.pcap into a list named r:

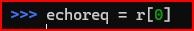
Next, I extract the only record in the list (r[0]) and assign it a name of echoreq
I assign the ICMP layer of the echoreq an attribute sequence number value of 4321 and display it.

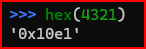
Scapy displays the ICMP sequence number in hex, so I can validate that 0x10e1 is equivalent to decimal 4321:
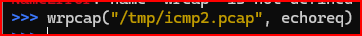
Next, I use wrpcap() to write echoreq to /tmp/icmp2.pcap and use tcpdump in verbose mode to read the record.
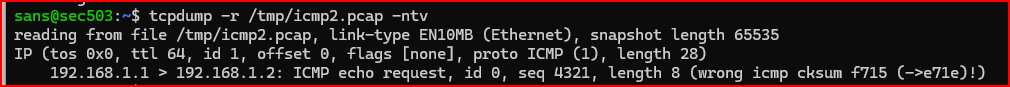
2. When you view the resulting packet in the new /tmp/icmp2.pcap file with tcpdump, you should be able to identify an obvious problem with the packet. What is it?
The checksum is corrupted.
3. Why did this happen ?
I altered the ICMP sequence number value and did not get scapy to recompute the checksum after that. The checksum value is not recomputed until the frame is either or stored to a pcap file.
4. Correct the issue by altering the record that still exists in your Scapy interactive session and writing it out again to /tmp/icmp2.pcap.
I need to delete the checksum value from the ICMP header
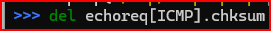
Now, I can write it out again
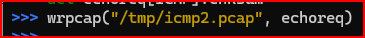
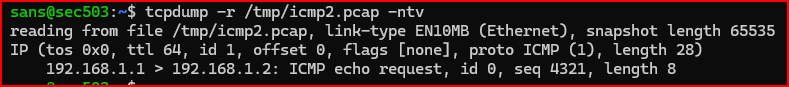
5. Rerun tcpdump to make sure the error was corrected
Exercise 3
Description: This exercise requires you to craft and send some crafted traffic using Scapy. Specifically, you craft an ICMP echo request in one Scapy interactive session, listen for it in another Scapy interactive session, and respond with a crafted ICMP echo reply from the second session.
You need to open three different ssh connections to the virtual machine for this. If you still have Scapy running from the previous exercises, using sudo scapy, this can be the first ssh connection.
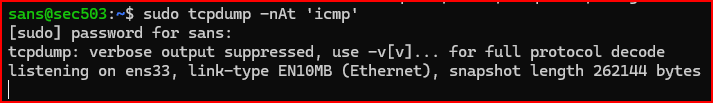
In a second terminal, use tcpdump to sniff for the traffic you will craft and send from the Scapy sessions from the other two terminals. Unlike simply reading a pcap as we have been doing, sniffing traffic using tcpdump requires you to have elevated privileges. Like with Scapy, use sudo to elevate your privileges when running tcpdump to sniff traffic off an interface. The below tcpdump command sniffs for traffic and disables DNS name resolution with the -n option, suppresses the timestamp display with the -tt option, shows you the ASCII payload with the -A option, and filters for ICMP traffic only. You do not need to specify the interface to sniff on if you are sniffing on the first Ethernet interface
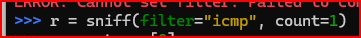
In the third ssh session, invoke a second Scapy interactive interface and prepare Scapy to sniff an ICMP echo request that you will send from the first Scapy session.
The Scapy sniff listens on a given interface for packets and you can add BPF filters with the filter option. Run the below command in Scapy.
- In the first Scapy session, craft an ICMP echo request with a source IP address of “172.16.1.1”, a destination IP address of “192.168.200.200”, an ICMP ID value of 10, and an ICMP sequence value of 100. Add any string payload to this, enclosing it in double quotes. Now, send the crafted ICMP echo request.
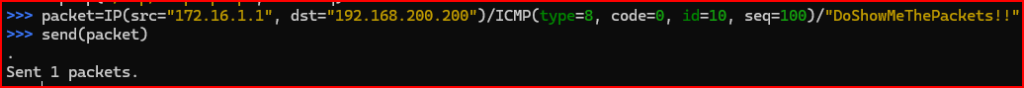
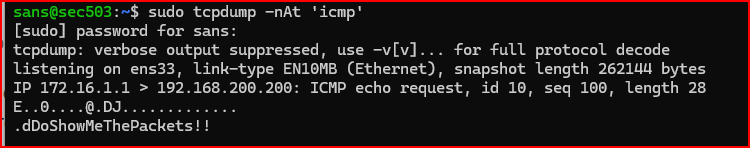
This is what I see in the tcpdump window
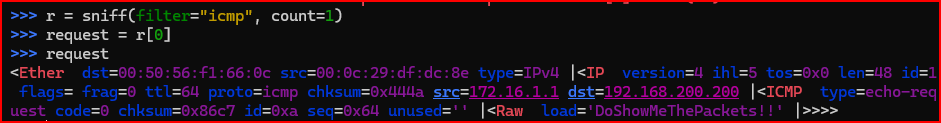
2. Return to the Scapy interface that sniffed the packet. Display the received ICMP echo request to find the ICMP ID value of 10, displayed as 0xa, and the ICMP sequence number of 100, displayed as 0x64.
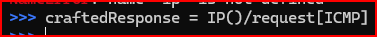
3. Continuing in the Scapy session, craft and send an appropriate ICMP reply. Make use of the ICMP echo request that Scapy captured, modifying fields as necessary. You should build a new IP header, but reuse the ICMP header and payload from the captured packet.
First,I need to create a new IP header and stack that with the captured ICMP request and payload
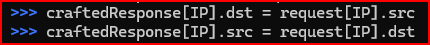
Next, I need to set the source of this new IP packet to be whatever the destination address was in the request. I also need to set the destination address for this new IP packet to be the source of the captured request.
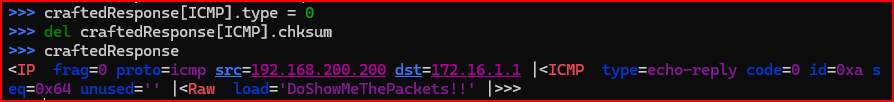
Finally, since I want to send an echo-reply, I need to set the ICMP type to be 0. I also need to delete the ICMP checksum value, which was copied from the original packet. I want Scapy to automatically recalculate this value so that a checksum error does not get generated.
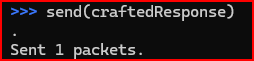
Now, I can send my packet
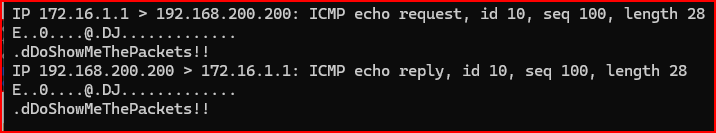
4. Verify that your crafted echo reply was properly sent by checking the tcpdump output from the other window.
Leave a Reply