Given the time spent mastering signature-based detection, signatures are a very familiar starting point, and signatures can certainly play a role in Zeek scripts and logs. Our objective is to create a simple signature and configure Zeek to use this signature to detect content.
Exercise 1
Description: Create a signature to find the dnscat proof-of-concept covert channel. This form of dnscat can be easily identified by creating a signature that looks for the string dnscat in UDP DNS packets.
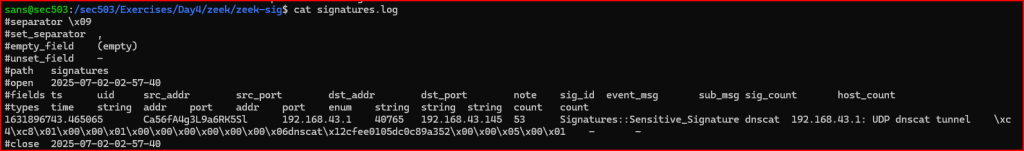
Zeek signatures are typically stored in files using the .sig extension. Please create a signature to log every time the word dnscat is seen in UDP DNS packets! Use the filename dnscat.sig for your signature. Run Zeek with this signature file and verify that it successfully logs events. Activity from this covert channel can be found in the signature.pcap file in the /sec503/Exercises/Day4/zeek/zeek-sig directory.
The general form of a zeek signature will be:
signature signatureName {
ip-proto == XXX # Fill in the correct IP protocol
dst-port == XXX # Fill in the correct DNS server port number
# Any other required IP, TCP, UDP, or other protocol headers go here.
payload /RegularExpression/ # Create a regular expression to find the content
event “Longer message” # An arbitrary message string to add to the log
}
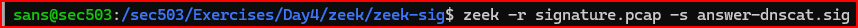
To tell Zeek to load a specific signature file, you must use the -s option: zeek -r capturefile.pcap -s signaturefile.sig.
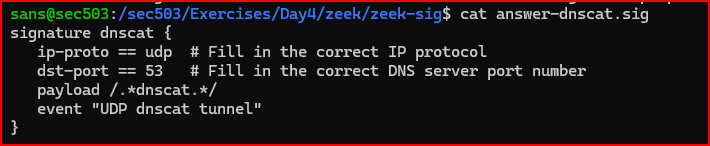
Putting it all together the signature, the signature could look like this:
signature dnscat{
ip-proto==udp
dst-port==53
payload/.*dsncat.*/
event “udp dnscat tunnel”
}
Let’s load this signature file
Leave a Reply