Details
During class we discovered that there was unusual activity on January 2, 2021. This leads to several important questions. Which way was the data moving? What does the data appear to be? Is this likely data exfiltration? We will answer these questions in this lab.
Exercise 1
In the course book, we saw that the anomalous activity occurs on Saturday, January 2, 2021.
- Begin by using SiLK to confirm that January 2, 2021 is an outlier. Query the repository for all of the data between March 1, 2020 and March 1, 2021. Use the SiLK tools to process the data to report the total number of bytes transferred over each 24 hour period.
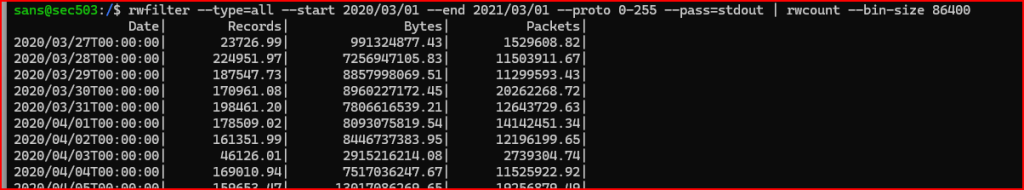
If I scroll down to the January 2,2021 line, I can easily see that there was an abnormal number of bytes transferred on this day confirming our assumption:
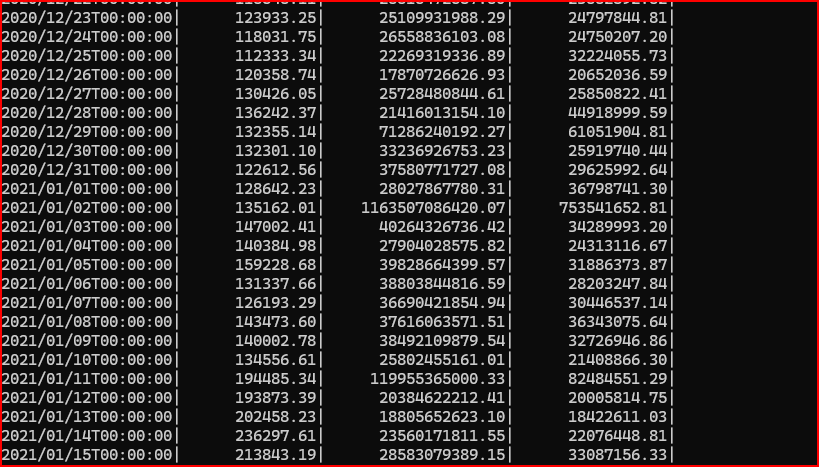
2. Now that you have confirmed what the tool reported, it’s time to drill into January 2, 2021. Identify when the greatest amount of data is seen moving on the network. During which hour does the greatest amount of data move?
I just to modify my last command line by changing the start and end date in rwfilter and change the bin size in rwcount:
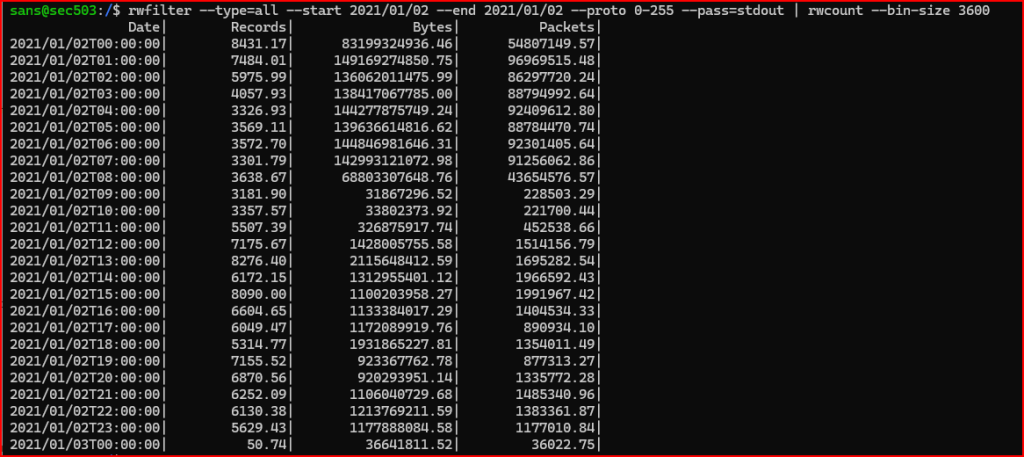
3. If you review the data that you find in step 2, you should see that the large amounts of data are being sent very early in the day. Please check the 24 period from 12:00 PM January 1 through 12:00 PM January 2 to check if the data flows begin on January 1.
I can specify a starting and ending hour on top my dates in rwfilter:
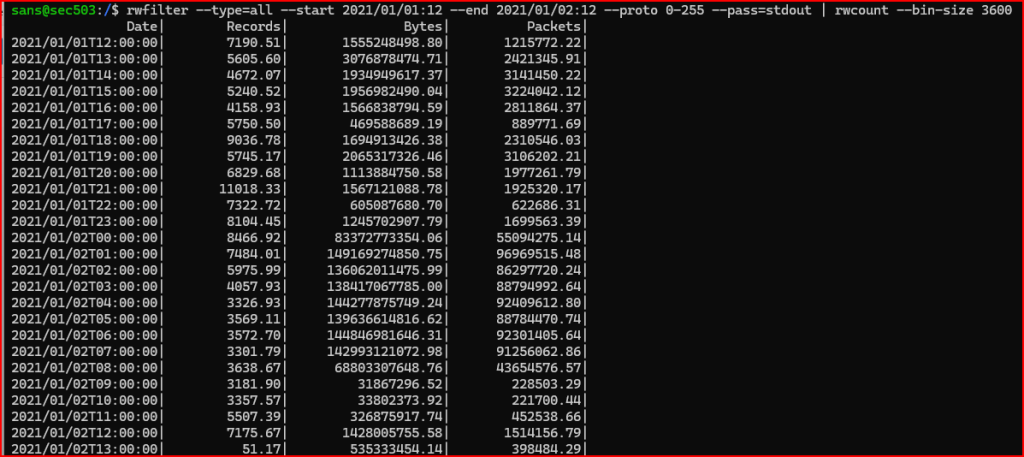
This confirms that the large amount of data being sent started right after midnight on January 2nd.
4. Satisfied that the large data transfer(s) are occurring on January 2, it’s time to examine what’s happening on January 2.
Examine the data between 00:00 and 12:00 on January 2. Which IP protocols are present and which of those transfers the greatest number of bytes?
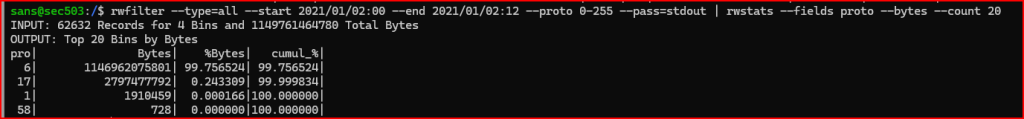
Out of the 4 protocols transferring data on that day, TCP (protocol 6) is the one transferring the greatest number of bytes.
5. The next task is to find the connection or connections involved. Using SiLK, determine which connection or connections are most likely creating this massive spike. You might find it most interesting to look at the top 20 connections.
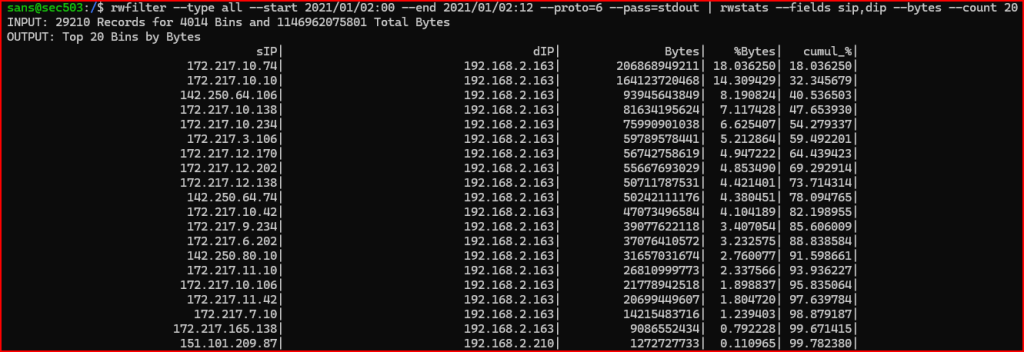
6. Examine the connections between 172.217.10.74 and 192.168.2.163. Also examine the records between 172.217.10.10 and 192.168.2.163. Answer the following questions:
- Is the data moving in or out of the enterprise?
- What seems to be the purpose of the communication?
- Does this appear to be something automated or something human driven?
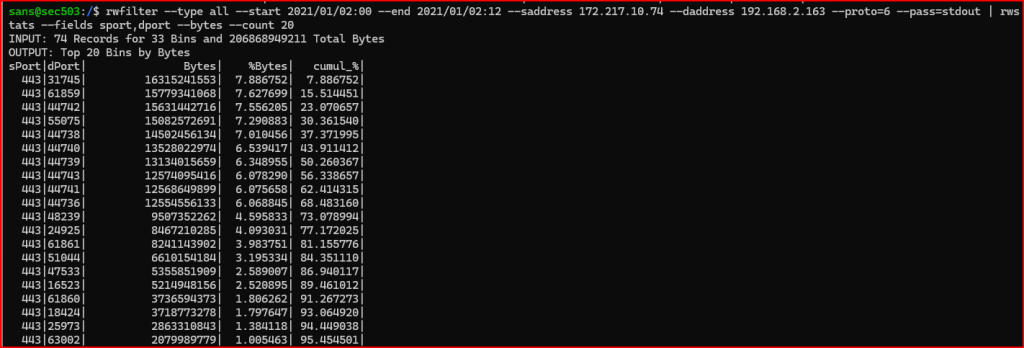
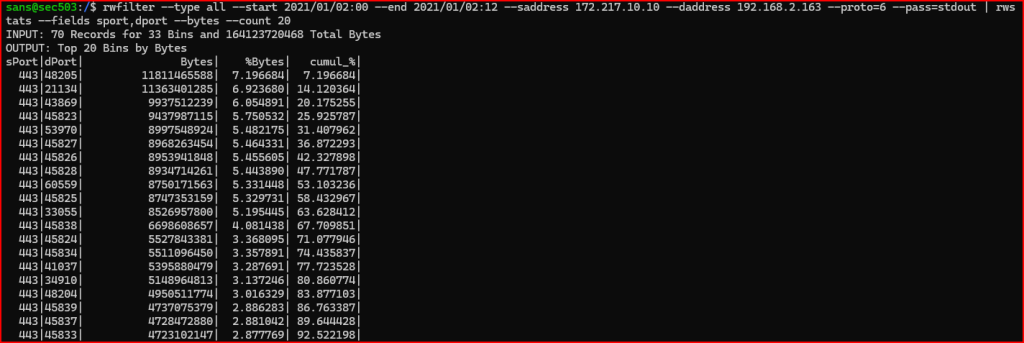
The first thing that I noticed was that the communication between these hosts, at least for more than 95% and 92% of their communications, is over port 443.
• Is the data moving in or out of the enterprise?
- We were provided with a network diagram during the class therefore I know that 192.168/16 is an internal network and the 172.217.10.74 and 172.217.10.10 is not within the enterprise. The data is moving in the entreprise.
• What seems to be the purpose of the communication?
- It is easy to say this is TLS communication over port 443. These appear to be large file transfers. We have many connections with a large amount of data in each. Finally, performing a
whoison 172.217.10.74 and 172.217.10.10 show that the addresses are assigned to Google. It could mean that somebody is streaming Youtube videos from inside the network this is YouTube related, but it could also be some type of Google Drive synchronization.
• Does this appear to be something automated or something human driven?
- Based on how quickly the connections seem to restart, it appears as some type of automated activity rather than being human driven.
Leave a Reply