Objectives
This exercise introduces you to a machine learning/AI pipeline solution that pushes data from Zeek through an AI model to produce alerts about network activity.
Details
This lab will require us to start several SSH connections to the virtual machine. One of these will run Zeek, monitoring the loopback interface. Another will run a Python script that will load a trained AI model and use it to generate alerts regarding network protocols that are present. The last connection will be used to replay packets over loopback so that Zeek has something to look at.
Exercise 1
To begin with, we need to get three separate command lines established to the VM.
- Please either open three separate SSH connections to the VM or, alternatively, use
tmuxto split your current connection into at least three panes. Use thecdcommand to change into the/sec503/Exercises/Day5/aidirectory in each session. - Now that we have three command lines available, we can start setting up the various pieces required to make this work. One of the sessions will be running Zeek and using the
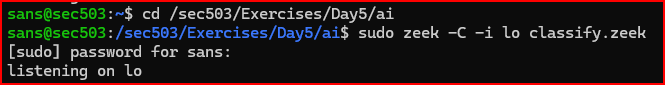
classify.zeekscript. This script will push the first bytes in every network stream into a Broker channel named/sec503/content. To use it, we need to start Zeek, ask it to listen on theloor loopback interface, and configure it to run this script. When we run Zeek on loopback, we will also see warnings related to checksums. While we would never do so in production, we will tell Zeek to ignore checksums while running in this lab. Please execute the following command as root in one of the sessions:
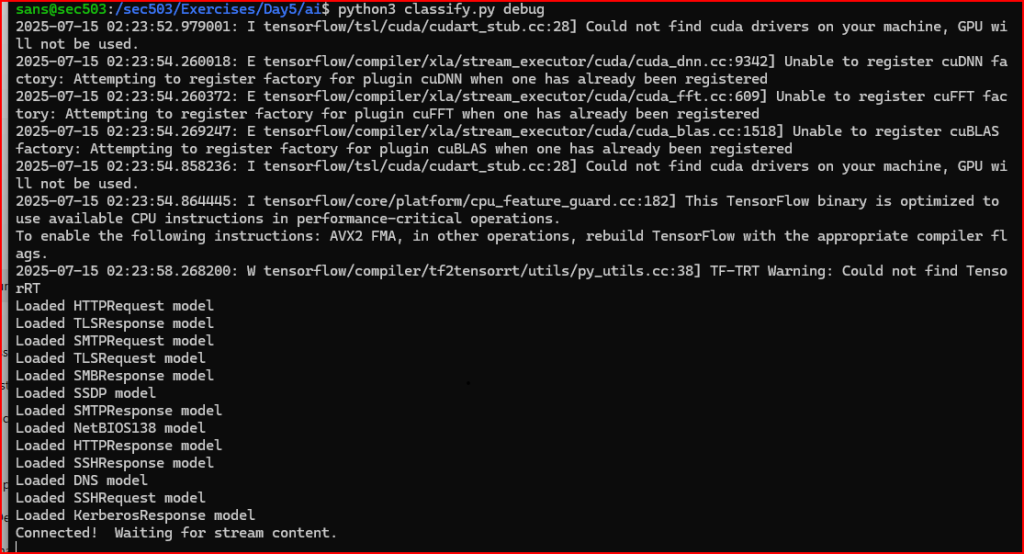
3. Now that Zeek is running, we can use another one of our sessions to connect the AI classifier to the Broker channel. We will do this using the classify.py script in the lab directory. Please run it as follows:
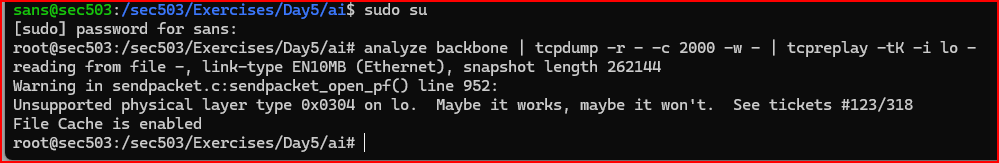
4. Our final task is to send data over the loopback interface so that Zeek can see it, relay the sessions to the classifier, and the classifier can report what it is seeing. To do this, you will use your third session. This session must be running as root.
5. Observe the output in the session that is running the classification script:
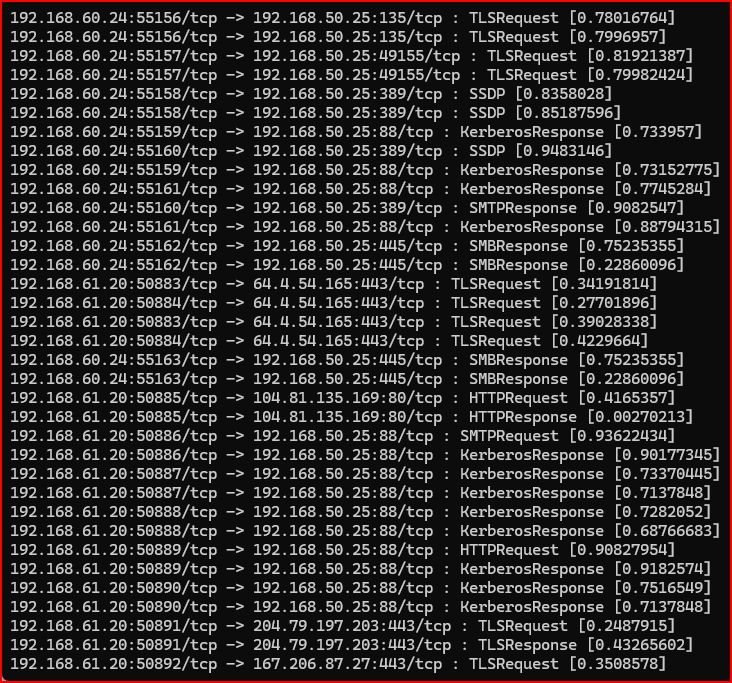
While there are some protocols being misclassified, overall this tool is doing an excellent job identifying known protocols.
Leave a Reply