Background
Some of the hosts on the monitored network are forced to pass through a transparent tls proxy. Our general practice is that we prefer not to decrypt tls packets unless something motivates us to do so, so we generally store the packets as is (encrypted). We also store the accompanying tls premaster secrets (the keys to the sessions) for as long as we retain the packets. This allows us to inspect specific sessions as needed without overly worrying about privacy issues since we maintain the premaster secrets in a separate, secure location. Not all of the sensors in the packet repository are subject to this.
Exercise 1
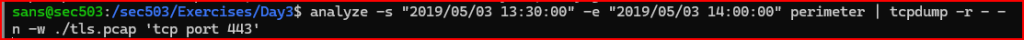
Use the analyze tool to extract the https packets (tcp port 443) from the perimeter repository for the time range 2019/05/03 13:30:00 to 2019/05/03 14:00:00 and store them in a file named tls.pcap.
Exercise 2
Download and open the tls.pcap file in Wireshark. Verify that the TLS sessions are encrypted using the Follow TCP Stream and Follow TLS Stream options.
First, I need to locate the first TLS connection where the handshake is seen. In Wireshark, I can use the tls.handshake filter to find it pretty quickly:
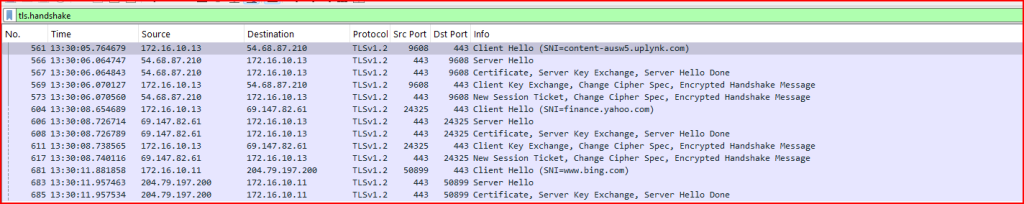
The first TLS handshake that is visible is located in packet 561. Using the Follow TCP Stream option, I can now follow the stream:
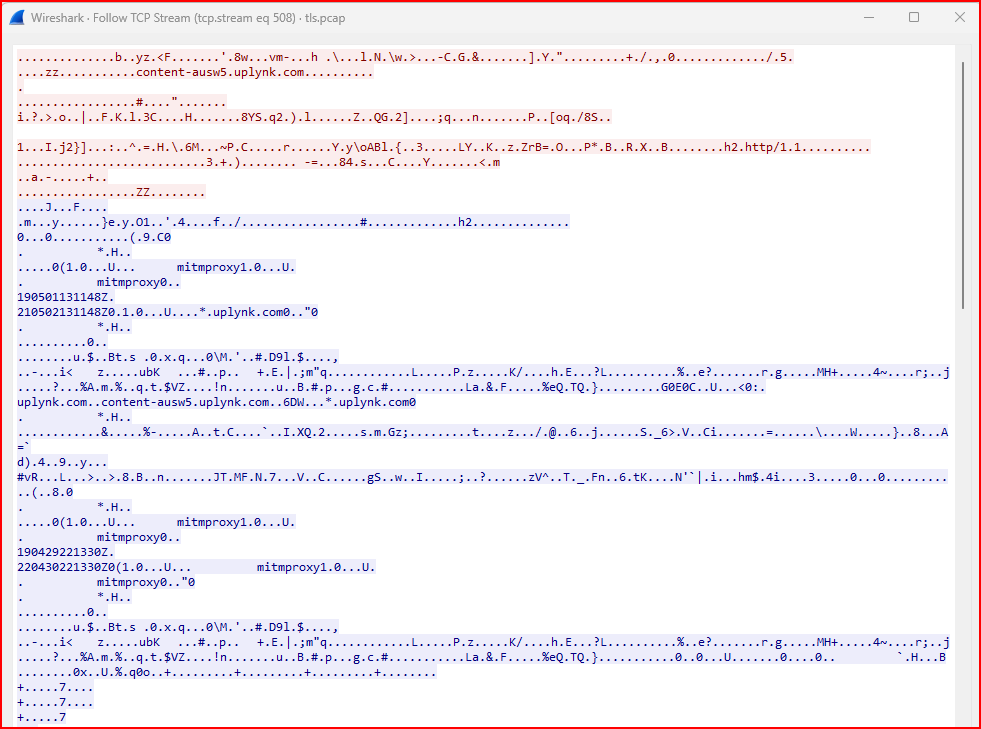
This data has some readable parts. Is it encrypted? Let’s use the Follow TLS Stream option on this same session.
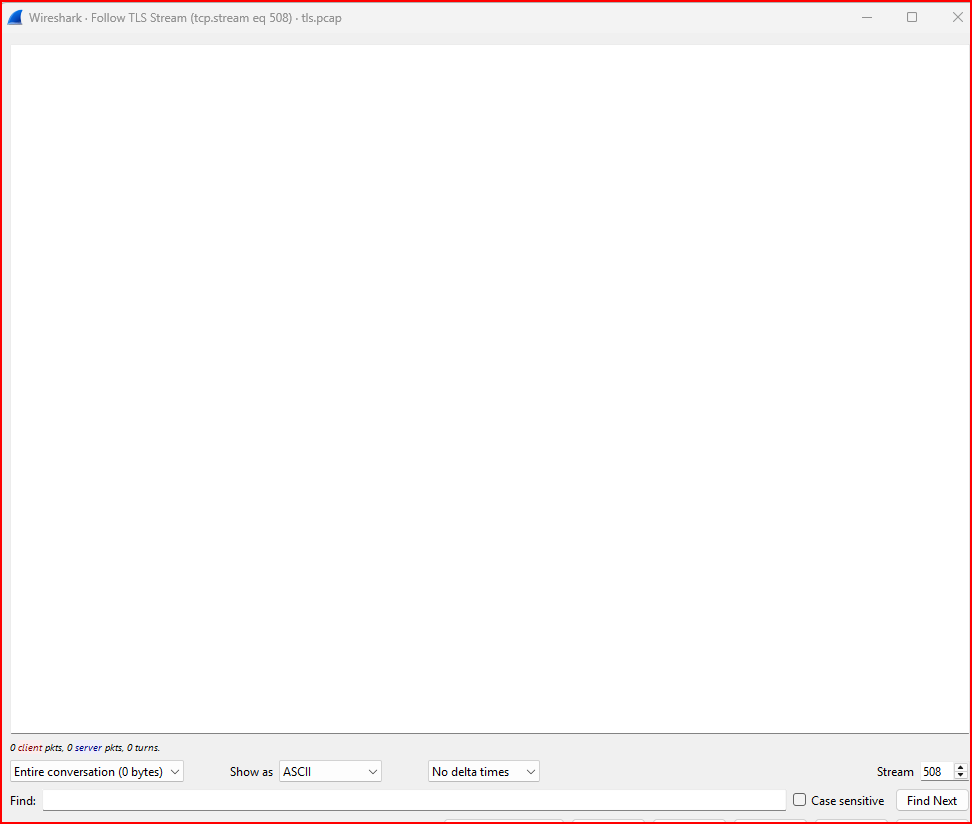
I see a blank window which ensures that the data is indeed encrypted and that I do not have the correct key to decrypt it.
Exercise 3
Using the tls.pcap file and the sslkeylogfile.txt in the /sec503/data directory, decrypt the first session in the capture file where the tls handshake was captured. What kind of data is found in this session?
I have to first configure Wireshark protocol preferences for TLS to use this txt file to decrypt the TLS sessions in the tls.pcap capture:
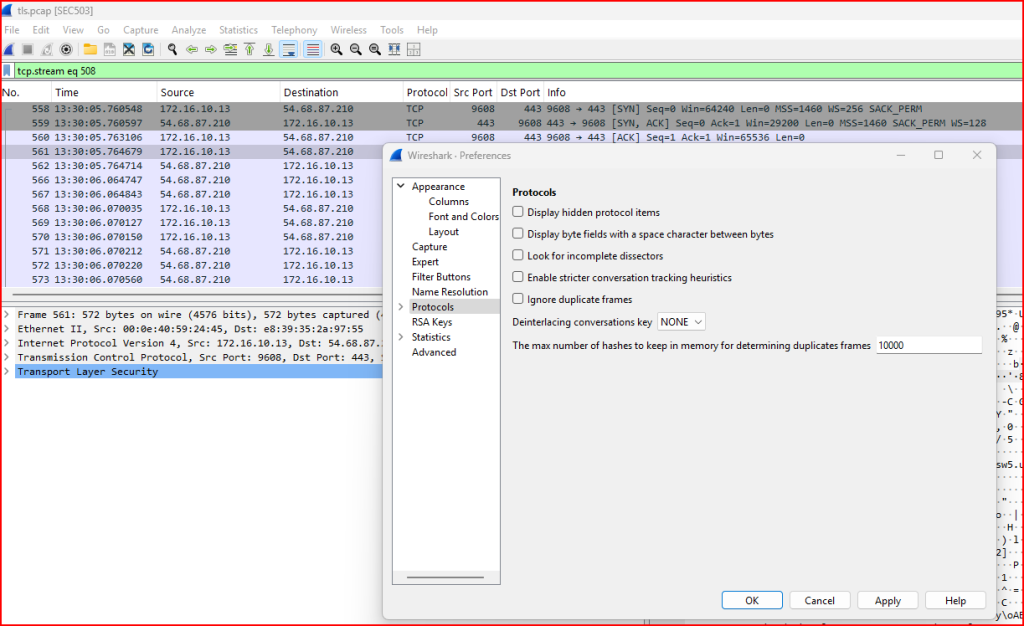
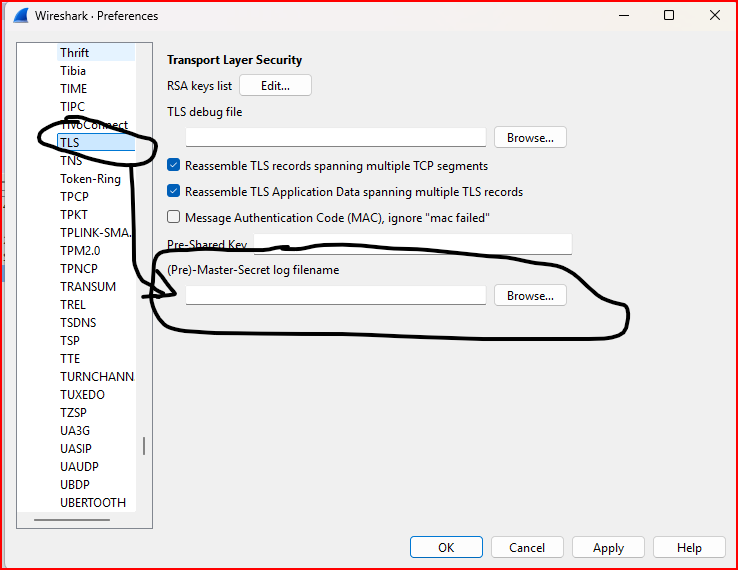
The Pre-master secret is now configured and I can go back to the first TLS handshake and Follow the TLS Stream:
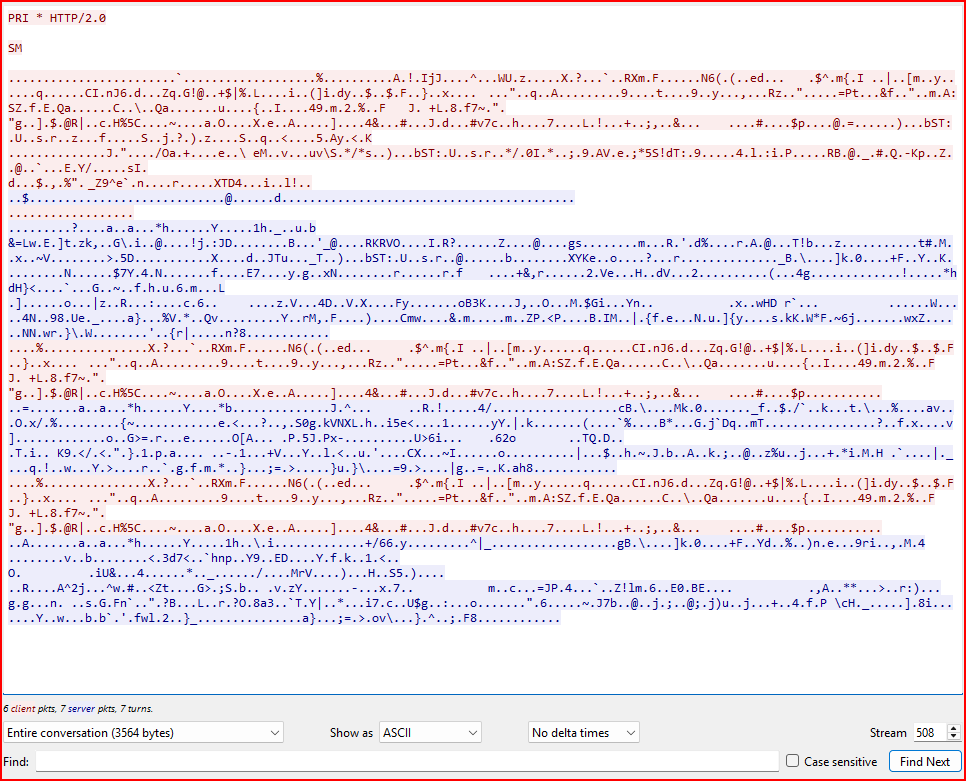
The window is not empty anymore and I see that the protocol used inside the TLS session is HTTP 2.0.
Exercise 4
Locate the first GET request in this traffic. What is the URL that is requested ?
Knowing that the protocol used is HTTP 2.0, I can apply the following display filter to the tls stream that I have already Identified:

Expanding the HTP2 portion, I can find the URL being requested:

Leave a Reply