Wireshark Display Filters Lab – Overview and Setup
This lab focused on becoming more familiar with using Wireshark display filters to isolate specific types of traffic.
Exercise 1 – Filtering DNS Queries for a Specific Domain
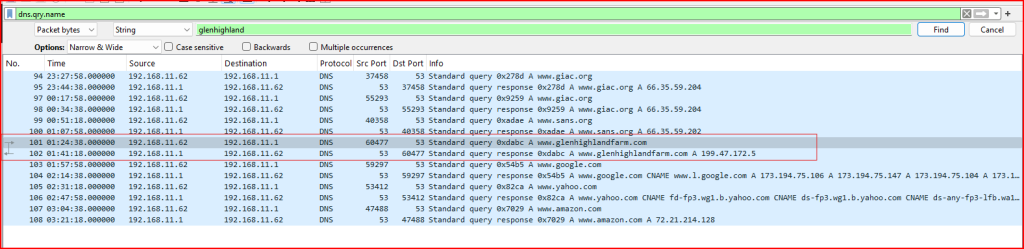
Task: Find the packet record number(s) where a DNS query name contains the string glenhighland.
There are many ways to solve this. One way is to filter the packets in Wireshark for DNS query name using the filter ‘dns.qry.name’ and then looking for the glenhighland string in the filtered packets using the Edit/Find Packet menu. Packets 101 and 102 contains this string.
Exercise 2 – Finding ARP Request Records
Task: Find all ARP request records. How many are there, and what filter did you use?
To complete this task, I used a Wireshark display filter that isolates ARP request packets specifically. First, I reviewed the structure of an ARP packet by looking at one in the packet list which Wireshark identified as a request under the Address Resolution Protocol section.
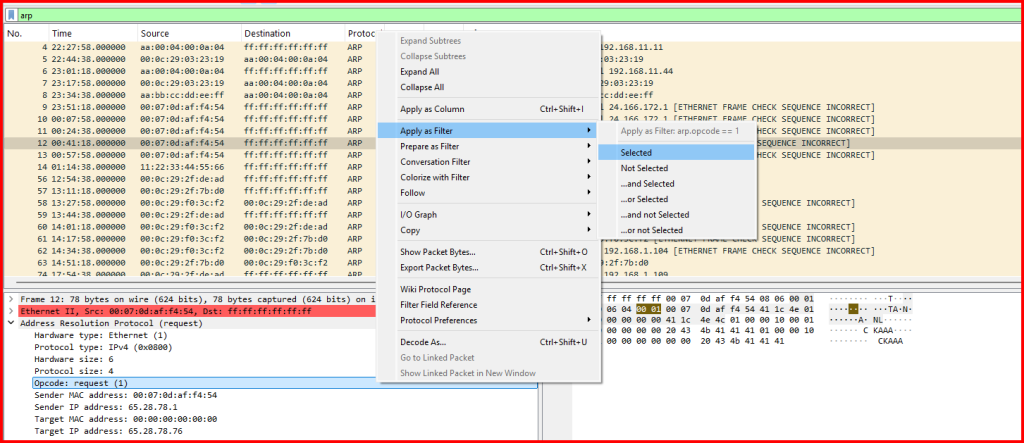
I then right clicked on the Opcode line and applied this same filter to the packet list.
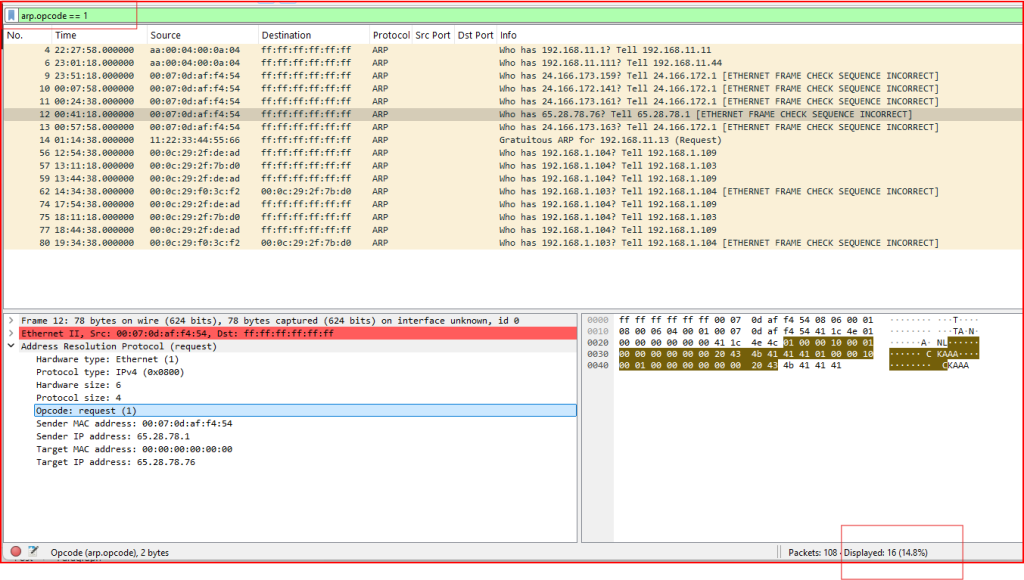
The arp.opcode==1 gets applied, and 16 packets get displayed (it is shown at the bottom right corner of the wireshark screen).
Exercise 3 – Identifying ICMP Echo Replies with Undersized IP Payloads
Task: Find the record numbers of any ICMP echo reply (type 0) frames that required zero-padding due to being smaller than the minimum acceptable Ethernet II length.
To solve this, I first recalled that the minimum Ethernet II frame size is 64 bytes, and that the Ethernet header (14 bytes) plus trailer (4 bytes) leave at least 46 bytes required for the IP payload. Therefore, any IP datagram smaller than 46 bytes would be too short and must be padded to meet Ethernet’s minimum.
I used the Wireshark Display Filter Expression dialog to build a compound filter that would identify:
- ICMP echo replies (type 0)
- IP datagrams with a Total Length < 46
To do this:
- I opened Analyze > Display Filter Expression
- Selected the field ip.len
- Chose the less than (
<) relation - Entered the value
46 - Added icmp.type == 0 to narrow it to echo replies
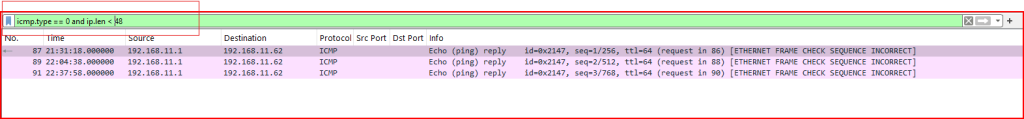
We identified 3 packets using these combined filters.
Exercise 4 – Isolating and Exporting DNS over UDP Traffic
Task: Find all records where the UDP protocol is carrying DNS traffic. How many are there? Save those packets to a new file named dns.pcapng.
To complete this, I used this display filter in Wireshark:
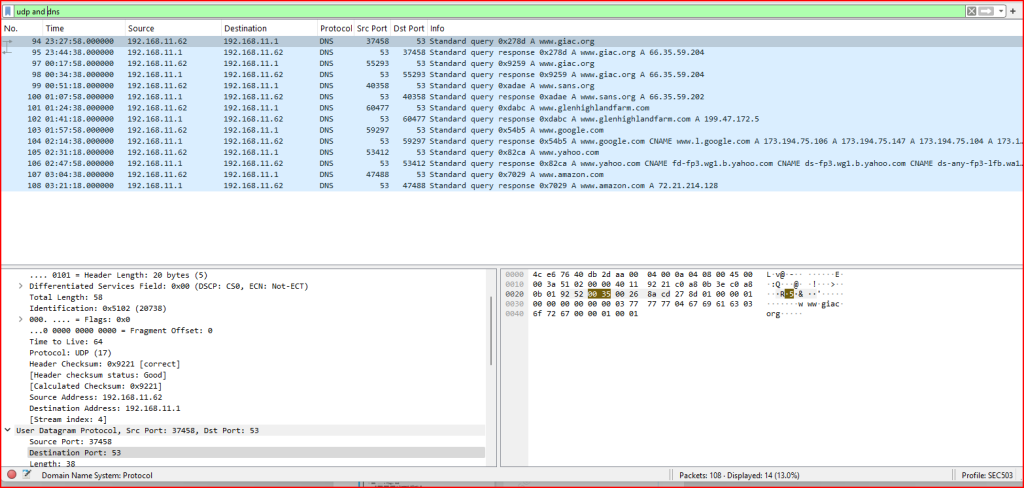
This filter shows all packets where DNS communication is occurring over UDP (14 packets are displayed).
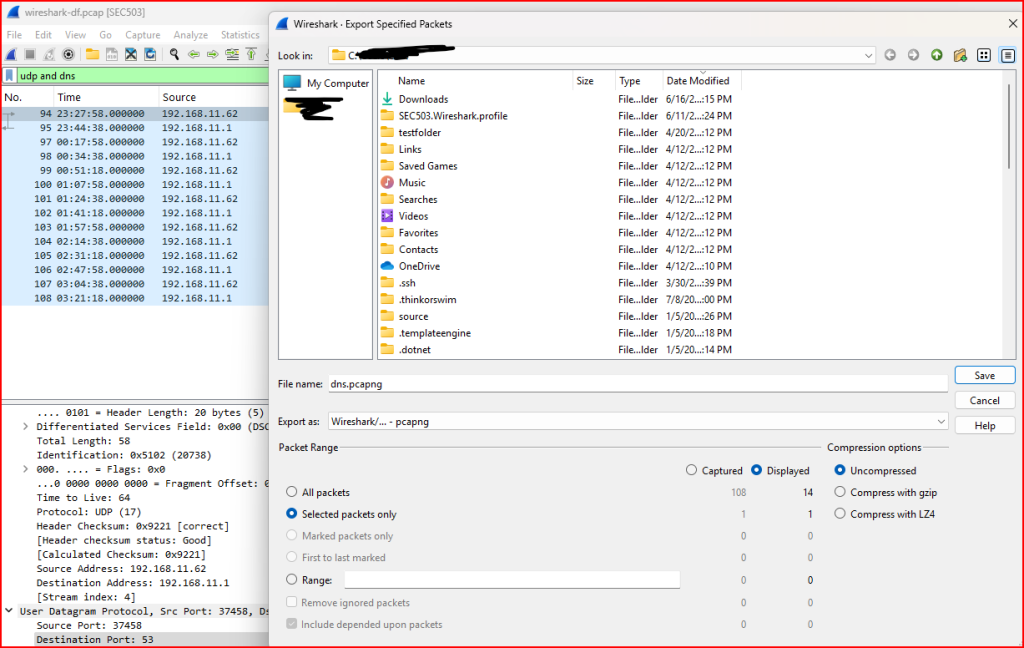
Once filtered, I saved the displayed packets to a new capture file:
- Went to File > Export Specified Packets.
- Entered the filename:
dns.pcapng. - Selected All packets and Displayed (to export only the filtered results).
- Clicked Save.
Leave a Reply