This lab focused on building familiarity with tcpdump filters, particularly for identifying specific traffic based on TCP flags. The lab also introduced the use of TCP flags, which play a key role in identifying different types of TCP traffic (e.g., SYN, ACK, FIN).
Exercise 1 – Identifying TCP Connection Attempts with tcpdump
Objective:
Use tcpdump to examine records from the file int-server.pcap and identify initial TCP connection attempts from clients to servers. The goal is to isolate packets where only the SYN bit is set—this indicates the start of a TCP handshake.
Steps Taken:
- Command Setup:
To simplify the output, I used the-n(no DNS resolution) and-t(no timestamp) flags - Filtering on TCP Flags:
- TCP control flags are located at byte offset 13 in the TCP header (
tcp[13]). For SYN-only packets (i.e., no ACK or other bits set), we need to match exactly the binary value 00000010, which is 0x02 in hex. - tcpdump Filter Expression:
- The appropriate filter to match only SYN packets is:
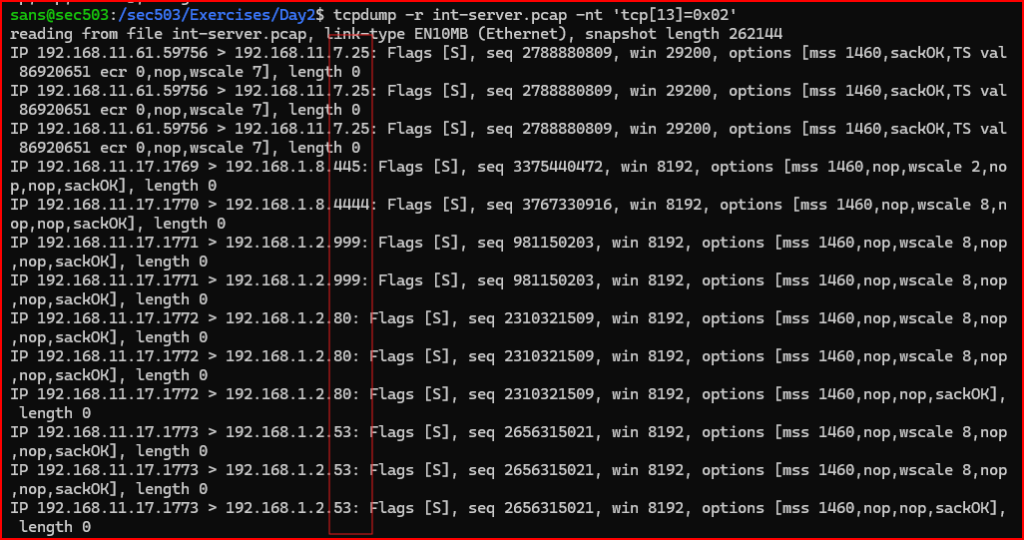
We see attempted connections from the clients to ports 25(SMTP), 445(SMB), 4444(default port used by Metasploit), 999, 80(HTTP) and 53(DNS).
Exercise 2 – Filtering for TCP SYN-ACK Responses
Objective:
Use tcpdump to identify packets from the int-server.pcap file where a server responds to a connection request—i.e., where both the SYN and ACK flags are set. This indicates the server is listening and willing to establish a connection.
Understanding TCP Flags:
- The TCP flags byte is at offset 13 (
tcp[13]) - ACK = 0x10
- SYN = 0x02
- Therefore, SYN-ACK =
0x12(00010010 in binary)
tcpdump Filter Used:
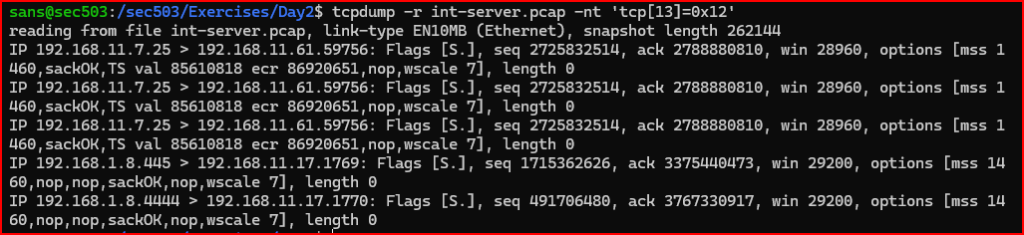
The server ports that responded are 25, 445 and 4444.
Exercise 3 – Filtering for TCP Session Termination (RST or FIN)
Objective:
Use tcpdump to identify packets from the int-server.pcap file that contain termination flags, specifically the RST or FIN flags. These flags signal that a TCP session is being closed—either gracefully (FIN) or abruptly (RST).
Flag Values:
- FIN =
0x01 - RST =
0x04
Unlike previous filters that matched exact values, this task required detecting whether either of the two termination flags is present, regardless of other flags that might also be set.
Using a Mask Byte:
The correct approach is to apply a mask byte that preserves only the FIN and RST bits:
- Binary:
00000101 - Hex:
0x05
The filter will check if either of these bits is present using a bitwise AND mask.
tcpdump Filter Used:
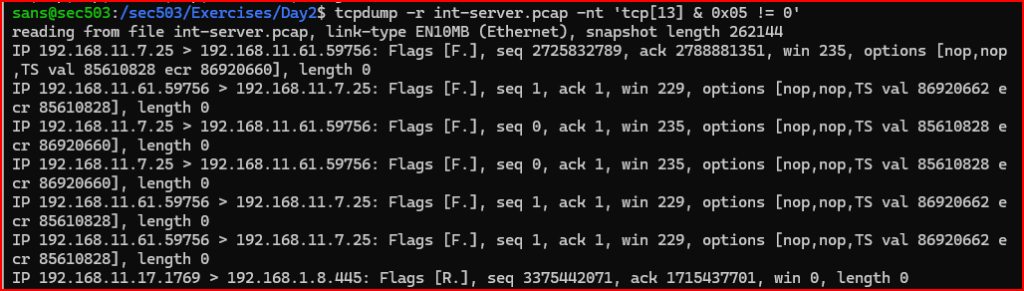
We see 7 records with either or both the FIN and RESET flags set.
Exercise 4 – Filtering for TCP Packets with Both PSH and ACK Flags on Port 143 (IMAP)
Objective:
Use tcpdump to extract the first five packets from int-server.pcap that meet all the following criteria:
- Destination port is TCP 143 (IMAP)
- Both the PUSH and ACK flags are set
- Other flags may be present as well
TCP Flags Reference:
- ACK =
0x10(bit 4) - PSH =
0x08(bit 3)
Combined, they yield a value of0x18(00011000 in binary)
To isolate packets where both these bits are set (regardless of other flags), I used a bitmask to mask all other bits:
- Mask:
0x18 - Value:
0x18
tcpdump Filter Used:
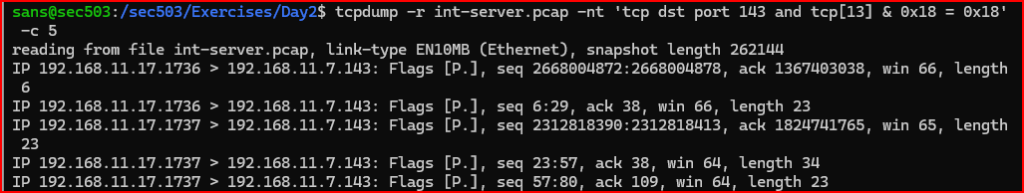
Leave a Reply